A Foreman proxy (that is the upstream software of the Red Hat Network Satellite Server 6 Capsules) is a server that mirrors the contents from Katello. It's primary aim is to facilitate content federation across various geographical locations, but it is often used to:
- decrease the load on the central Katello server
- reduce bandwidth usage onto geographical links
- increase redundancy, and also to achieve a fine grained segregation level that may be required by some regulatory
Unless you are working in a quite small and not geographically distributed environment, it is very likely that you must provision a Foreman proxy sooner or later.
Provisioning Foreman proxies, same way as installing software in general, is a typical time consuming and error prone task that is often convenient to automate in some way.
As we already saw in the previous post, we can install Foreman proxy using Ansible having it to:
- ensure that the target systems meet the minimal requirements
- automatically partition the systems in the most convenient way
- install everything taking in account of using the right versions of the involved packages so as to avoid installation failure because of wrong dependencies
- set up all the configurations that are required to improve the usability of the installed environment
- take care of issuing all the necessary statements to configure a Foreman proxy (a Capsule) on Katello (the Satellite) and automatically provision it
This is the second part of the "Install Katello Using Ansible" post: we are about to see how the playbooks developed in that post can be used to easily install Foreman-proxy using Ansible.
Prerequisites
Same way as Katello, also Foreman proxy is a massive suite that demands a high amount of CPU and RAM.
The very minimum requirements of the Foreman proxy node are:
- 4 cores
- 12 GB of RAM
- 4 GB of swap space
- enough disk space to store the packages that are mirrored by its repositories
As you can easily figure out, the Foreman proxy does require a lot of GB of disk space not because of the software itself, but for the amount of data required by the packages and images it mirrors from Katello when providing local software repositories. It is straightforward that the best approach is using LVM to manage the disk space, since these systems will keep on demanding more and more disk space as time passes by.
In this Lab we use the "system" Volume Group, that is the one used by the base platform, but you may of course prefer using a dedicated Volume Group; about the sizing, in my opinion a LVM Volume Group with at least 100GiB is a good starting point.
If your Volume Group is not big enough, you can extend it by attaching additional disks after marking them as Physical Volumes.
In this post we provision Foreman proxy onto the sat-ci-up3a003 target host: before we extend the "system" Volume Group by adding the /dev/sdb disk:
sudo pvcreate /dev/sdb
sudo vgextend system /dev/sdbThe Ansible management station - sat-ci-up3a002, where we already installed Katello, reaches the hosts where to install the Foreman proxies using SSH; the automation connects using the "ansible" user using sudo for privilege escalation when needed.
Since this user does not exist on the target systems right after the operating system installation, the site.yml playbook runs two distinct plays:
- the first connects as the "root" user and creates the "ansible" user, authorizes its SSH key and configures the required sudo rule to grant administrative rights to the "ansible" user.
- the second play connects as "ansible" user and performs the actual installation and configuration
This mean that on the target hosts we must set an initial password for the root user (in this Lab the password is "grimoire"): just connect to the sat-ci-up3a003 host as root (or switch to the root user) and issue:
passwdremember the password you typed, since we have to add it to the Ansible-vault protected secrets file as we'll see very soon.
Connect To The Katello Host
Since we are reusing the playbooks we developed in the "Install Katello Using Ansible" post, we do not need to code anything: we just have to become the ansible user, perform a little bit of configuration and eventually run them.
Just connect to the Katello host - sat-ci-up3a002 in this posts - and switch to the "ansible" user:
sudo su - ansiblethen change directory to "katello":
cd katelloInstall Foreman Proxy Using Ansible
After the preface, we are ready to configure and use the playbooks contained in this directory.
Configuring Ansible For Using SMART Connections
In this Lab we have already installed Katello on the sat-ci-up3a002 host, that is the Ansible management station too: in such a scenario, since the management station and the target host are the same, it just requires a local connection.
Foreman proxies are instead installed on hosts that are different from the Ansible management station, so it is straightforward that an SSH connection is required to interact with them. Please mind that in Ansible terms, an SSH connection is often said to be a "smart" connection.
This means that we need to generate the RSA key-pair of the "ansible" user for authenticating when connecting to these target hosts:
ssh-keygen -b 2048 -C 'ansible automation service user' -f ~/.ssh/id_rsaAdding The Foreman Proxy Node To The Ansible Inventory
In this post we provision Foreman proxy onto the sat-ci-up3a003 target host: we must of course add it to the hosts text file of the "inventory" directory.
After adding it, the file must look like as follows:
sat-ci-up3a002 ansible_connection=local
sat-ci-up3a003 ansible_host=sat-ci-up3a003.mgmt.carcano.local
Please note that "sat-ci-up3a003" is just the name of the target in the inventory: we set the actual FQDN using the "ansible_host" attribute.
As we saw the first play of the site.yml playbook connect to the target hosts as the "root" user: we must add its password to the Ansible-Vault protected secrets file .
Type the command:
ansible-vault edit files/secrets.ymladjust the "root_user_password" attribute so that it matches the one you set on your target hosts.
The outcome must look-like as follows:
katello_admin_password: grimoire
root_user_password: grimoire
Besides adding the host to the inventory file, we must also provides all the necessary attributes to configure it: create the inventory/host_vars/sat-ci-up3a003.yml file providing settings specific to configure a it as foreman-proxy node:
katello_version: "3.12"
katello_scenario: "foreman-proxy-content"
katello_admin_user: admin
katello_cli_admin_user: katello
katello_hammer_api_host: sat-ci-up3a002.mgmt.carcano.local
server_domain: mgmt.carcano.local
provisioning_interface: eth1
provisining_network: "10.2.0"
katello_installer_extra_options:
- "--foreman-proxy-dns true"
- "--foreman-proxy-dhcp true"
- "--foreman-proxy-tftp true"
- "--foreman-proxy-dns-interface {{ provisioning_interface }}"
- "--foreman-proxy-dhcp-interface {{ provisioning_interface }}"
- "--foreman-proxy-dns-zone provision.{{ server_domain }}"
- "--foreman-proxy-dns-forwarders 10.0.2.3"
- "--foreman-proxy-dns-reverse {{ provisining_network.split('.')[2] }}.{{ provisining_network.split('.')[1] }}.{{ provisining_network.split('.')[0] }}.in-addr.arpa"
- "--foreman-proxy-dhcp-range '{{ provisining_network }}.10 {{ provisining_network }}.20'"
- "--foreman-proxy-dhcp-gateway {{ provisining_network }}.1"
- "--foreman-proxy-dhcp-nameservers {{ provisining_network }}.1"
katello_plugins:
- "--enable-foreman-proxy-plugin-remote-execution-ssh"
- "--foreman-proxy-plugin-remote-execution-ssh-install-key=true"
- "--enable-foreman-proxy-plugin-ansible"
storage_pools:
- name: system
disks:
- sda2
- sdb
volumes:
- name: pulp_cache
size: 13G
fs_type: xfs
mount_point: /var/cache/pulp
- name: pulp_data
size: 50G
fs_type: xfs
mount_point: /var/lib/pulp
- name: mongodb
size: 20G
fs_type: xfs
mount_point: /var/lib/mongodb
- name: qpidd
size: 5G
fs_type: xfs
mount_point: /var/lib/qpidd
note how this time we set the "katello_scenario" variable to "foreman-proxy-content": this value lets the Ansible automation know that we want to configure this host as a Foreman proxy.
Note also how a Foreman Proxy does need fewer dedicated mount points.
Provision The Foreman Proxy
Now that we properly configured everything, we can simply run ansible-playbook with the "install" tag (-t install), limiting the targets only to the "sat-ci-up3a003" host - we just need to type:
ansible-playbook --ssh-extra-args "-o StrictHostKeyChecking=no" -t install --ask-vault-pass --limit sat-ci-up3a003 site.ymlplease note that the --ssh-extra-args "-o StrictHostKeyChecking=no" command parameter is  necessary only for the first run on each Foreman proxy so to retrieve and trust the SSH host key of the Foreman proxy host.
necessary only for the first run on each Foreman proxy so to retrieve and trust the SSH host key of the Foreman proxy host.
You can relax with a cup of tea if you fancy: also installing and configuring everything on the Foreman Proxy takes quite a lot of time to complete.
Once everything completes the sat-ci-up3a003 host must be among the list of the available Foreman proxies: we can list them either using the Katello web-ui or the hammer command line utility; if using the Katello web-ui, login to the Katello web-UI with a user that has administrative rights and ensure that you have selected "Any Organization" and "Any Location".
Then select "Infrastructure" and finally "Smart Proxies": the list of every Foreman proxy available to this Katello server is displayed.
If you want to see a page with the summary information of a specific Foreman proxy, just click on its name.
For example, this is how the summary information page of the sat-ci-up3a003.mgmt.carcano.local does look like on my Lab:

By the way mind that Foreman proxies and Red Hat Network Satellite Server's 6 Capsules are actually the same thing: indeed the hammer command to list the Foreman proxies is:
hammer capsule listremember that the site.yml playbooks configures the "katello" user as the one to be used to issue hammer statements, so you must switch to the "katello" user before issuing the above command.
On my system the output is as follows:
---|-----------------------------------|------------------------------------------------|--------------------------
ID | NAME | URL | FEATURES
---|-----------------------------------|------------------------------------------------|--------------------------
1 | sat-ci-up3a002.mgmt.carcano.local | https://sat-ci-up3a002.mgmt.carcano.local:9090 | Pulp, Dynflow, Ansible...
8 | sat-ci-up3a003.mgmt.carcano.local | https://sat-ci-up3a003.mgmt.carcano.local:9090 | Pulp Node, DNS, Templa...
---|-----------------------------------|------------------------------------------------|--------------------------Reconfiguring The Foreman Proxy
As we already saw in the previous post, besides installing the Foreman proxy, the site.yml playbook can also be used to re-configure it. You may need to reconfigure it for example to enable other Foreman proxy plugins such as the Ansible plugin (a very handy plugin that enables the Foreman proxy to perform remote executions using Ansible).
This can be easily accomplished by adding the relevant foreman-installer options to the "katello_plugins" list in the hostvar inventory file.
As an example, let's enable the Discovery plugin: note that it requires the "Discovery" feature installed on the Katello itself, so first we have to modify the "katello_plugins" list in the inventory/host_vars/sat-ci-up3a002.yml file as follows:
katello_plugins:
- "--enable-foreman-plugin-remote-execution"
- "--enable-foreman-proxy-plugin-remote-execution-ssh"
- "--foreman-proxy-plugin-remote-execution-ssh-install-key=true"
- "--enable-foreman-plugin-ansible"
- "--enable-foreman-proxy-plugin-ansible"
- "--enable-foreman-plugin-discovery"
- "--enable-foreman-proxy-plugin-discovery"
we just added:
- the "--enable-foreman-plugin-discovery" directive to enable the Discovery feature on Katello itself
- the "--enable-foreman-proxy-plugin-discovery" directive to enable the Discovery feature on the Foreman proxy installed on the same host where Kastello is running
we can now the playbook, limiting it to the sat-ci-up3a002 target host:
ansible-playbook -t config --ask-vault-pass --limit sat-ci-up3a002 site.ymlwait until the reconfiguration completes - it takes a while: at the end of the run, our Katello server and its on-board Foreman proxy is reconfigured with the discovery plugin enabled.
Now we must configure the Discovery plugin on the sat-ci-up3a003 Foreman proxy too. This time modify the "katello_plugins" list in the inventory/host_vars/sat-ci-up3a003.yml adding only the "--enable-foreman-plugin-discovery" directive file as follows:
katello_plugins:
- "--enable-foreman-proxy-plugin-remote-execution-ssh"
- "--foreman-proxy-plugin-remote-execution-ssh-install-key=true"
- "--enable-foreman-proxy-plugin-ansible"
- "--enable-foreman-proxy-plugin-discovery"
and then run the playbook, limiting it to the sat-ci-up3a003 target host:
ansible-playbook -t config --ask-vault-pass --limit sat-ci-up3a003 site.ymlas you see this time we do not need to specify --ssh-extra-args the command line option.
Wait until it completes, then login to the sat-ci-up3a003 so that we can make sure both that the Discovery feature has been installed and that the hammer command line has been properly configured to be run on the Foreman proxy itself.
Once logged, switch to the "katello" user:
sudo su - katellothen type the following command:
hammer capsule info --name sat-ci-up3a003.mgmt.carcano.localthe output is as follows:
Id: 8
Name: sat-ci-up3a003.mgmt.carcano.local
URL: https://sat-ci-up3a003.mgmt.carcano.local:9090
Features:
Pulp Node
DNS
Templates
TFTP
DHCP
Puppet CA
Puppet
Logs
HTTPBoot
Dynflow
Ansible
SSH
Discovery
Locations:
Default Location
Organizations:
Default Organization
Created at: 2022/04/16 16:24:19
Updated at: 2022/04/16 16:25:01note that we logged in to the capsule only to make sure that the "katello" user has been properly configured so to use the hammer command line utility passwordless, but the same command, always as "katelloW user, can be issued from the Katello server itself (sat-ci-up3a002 in this post).
Assigning The Foreman Proxy To An Organization
Foreman proxies are assigned to the "Default Organization", so the very first thing to do is login  to the Katello web-UI with a user that has administrative rights and then assign the right Organization to the Foreman proxy.
to the Katello web-UI with a user that has administrative rights and then assign the right Organization to the Foreman proxy.
Right after login, ensure that you have selected "Any Organization" and "Any Location", then select "Hosts" and finally "All Hosts": the list of every host registered to Katello is displayed - the Foreman proxies are listed among them, since they are actually registered client hosts.
Select the Foreman proxy (sat-ci-up3a003.mgmt.carcano.local in this post), then click on the "Select Action" button and pick the "Assign Organization" option: a form gets displayed.
Select the "Carcano" organization and tick the "Fix Organization on Mismatch" option
Since we also have to assign a Location to this Foreman proxy, tick the "Remember hosts selection for the next bulk action", so to get this host already selected when the list of every host is displayed again.
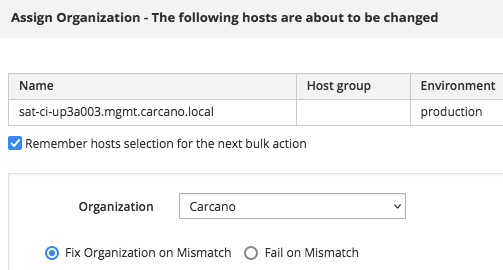
Click on the "Submit" button - you get back to the list of every host.
You may expect to be able to do the same task with the hammer command line utility, ... not quite: the answer is yes, but you need at least hammer v0.18: the "--organization" parameter is aimed only at specifying the scope of the hammer statement indeed.
Since hammer v0.18 the "--new-organization" option has been added right to let you change the organization using the command line.
So, with hammer v.018 or above the command is:
hammer host update --name sat-ci-up3a003.mgmt.carcano.local --new-organization CarcanoAssigning The Foreman Proxy To A Location
Same way as for the Organization, Foreman proxies are assigned to the "Default Location", so now we must assign the Foreman proxy to the right Location: in this post we assign it to the "SG - WR" datacenter. If it is not already selected, select the sat-ci-up3a003.mgmt.carcano.local host then click on the "Select Action" button and pick the "Assign Location" option: a form gets displayed.
Select the "SG - WR" location and tick the "Fix Location on Mismatch" option

Click on the "Submit" button - you get back to the list of every host.
Same way as for assigning an Organization using hammer, you need at least hammer v0.18 to be able to assign a Location to an host: the "--location" parameter is aimed only at specifying the scope of the hammer statement indeed.
Since hammer v0.18 the "--new-location" option has been added right to let you change the location using the command line.
So, with hammer v.018 or above the command is:
hammer host update --name sat-ci-up3a003.mgmt.carcano.local --new-location "SG - WR"Footnotes
Here it ends this tutorial on installing Foreman proxies using Ansible. As you see it is very convenient exploiting Ansible to provision them, since it can actually do everything, including reconfiguring the already provisioned Foreman proxies. Again, mind that everything shown in this post can easily be applied to Red Hat Network Satellite Server 6 capsules.
